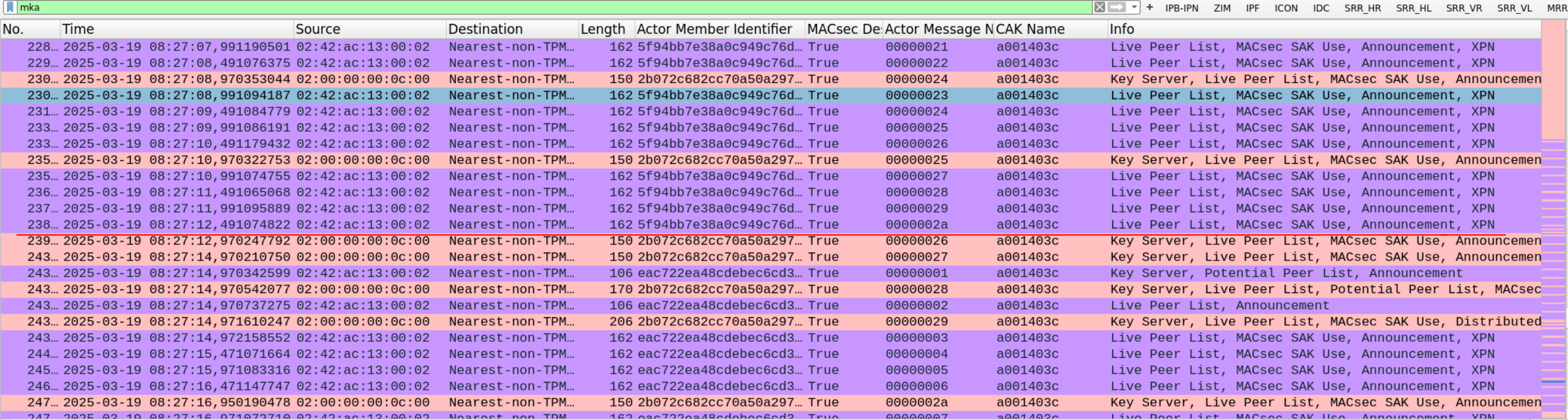
MKAD
MKAD overview
MKAD is a daemon from Technica that implements the MKA protocol as defined in the IEEE802.1X-2020 starndard. The daemon only works in Linux for now.
The daemon supports the following features:
All MACsec algorithms: GCM-AES-128, GCM-AES-256, GCM-AES-XPN-128 and GCM-AES-XPN-256.
EAP is not supported yet, but PSK is implemented.
Daemon executable
MTF Docker image
The MTF docker image should already include the MKAD daemon and the necessary libraries in order to be able to run it.
MKAD compilation
When using a manual installation of MTF, the MKAD must be compiled (or otherwise the executable copied) and the required libraries installed.
The compilation instructions can be found in the public repository: https://github.com/Technica-Engineering/MKAdaemon
In case of copying the compiled executable, the following libraries are needed to run it (not needed if compiled in the same machine since the dependencies will already be installed):
(They can be installed through “apt install”)
libnl-genl-3-dev
libbsd-dev
libglib2.0-dev
libnl-route-3-dev
libyaml-dev
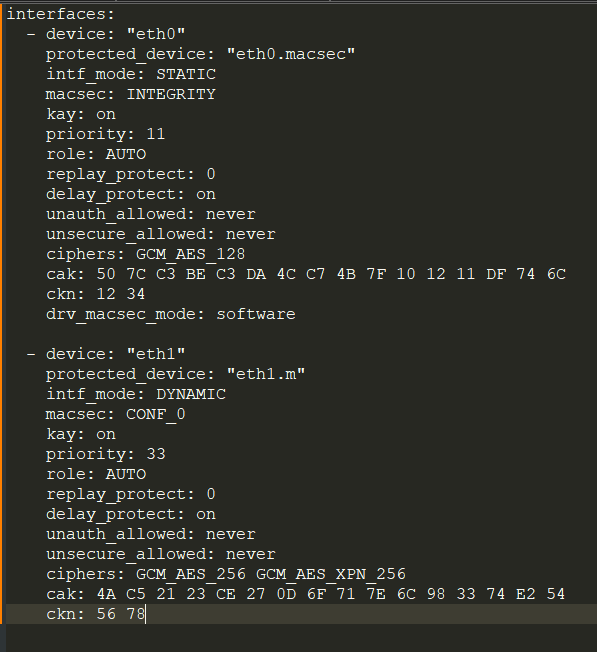
Configuration file
A configuration file must be specified when starting the daemon to configure the MKAD settings.
It is recommended to copy the file in the repository and modify it: https://github.com/Technica-Engineering/MKAdaemon/blob/main/mkad.conf.example
All settings are explained in the configuration file itself.
Global settings
These are located at the top part of the configuration file. Among other settings, These allow to specify the log level and the MKA protocol times (such as hello time or life time) These settings can usually be left as they are for a standard use case scenario.
Interface settings
These are located at the bottom of the configuration file. An interface entry must be specified for each channel that wants to be configured for macsec. Specially relevant parameters are the physical network interface (device), the macsec interface (protected_device) and the pre-shared key parameters (cak and ckn).
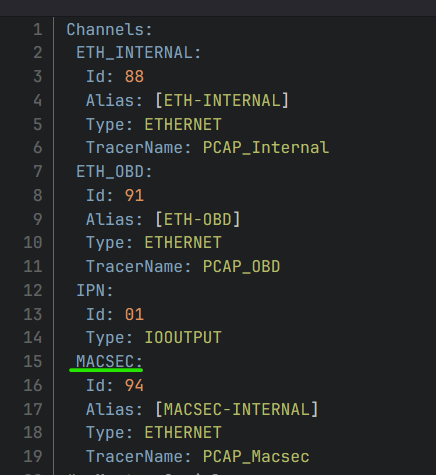
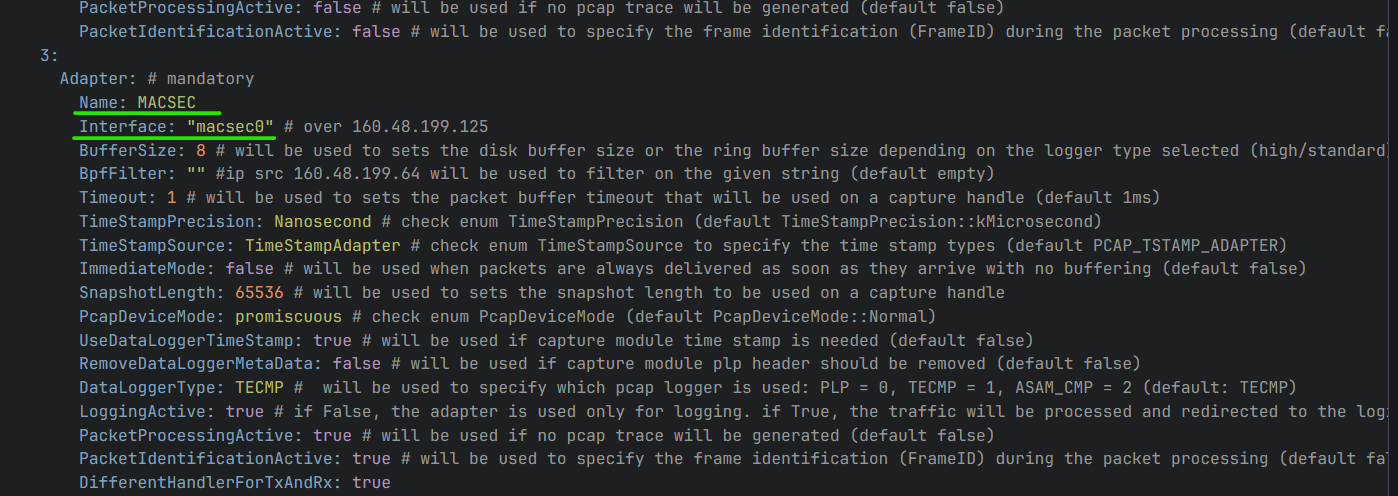
Additional MTF requisites
In order to allow MTF to use the MACsec interfaces that will be created by the MKAD, they must be specified in the channel mapping yaml file. They will be destroyed by the MKAD and created again with the proper parameters, but they must be present in the channel mapping at MTF start for it to be able to manage them properly.
DBUS system
The MKAD uses the Linux DBUS system, and it must be started before starting the MKAD for it to work properly.
It is possible that you may need to install the package libdbus-1-dev to be able to use it (apt install libdbus-1-dev).
Then, the following file https://github.com/Technica-Engineering/MKAdaemon/blob/main/dbus-policies/de.technica_engineering.mkad.conf must copied into the folder (create it if needed): /usr/share/dbus-1/system.d/
Some linux systems start automatically the DBUS system. In case it is not started (like in the case of Docker) it must be manually started. For that execute the following commands:
mkdir -p /var/run/dbus
dbus-daemon –config-file=/usr/share/dbus-1/system.conf –print-address
PyBinder MKAD controller usage
In order to use the MKAD from MTF, it only has to be imported from MTF PyBinder,
from mtf.libs.mtf_pybinder import mkad
started when needed (usually in the test case main function) specifying the configuration, file and channel name
mkad.start("./mkad.conf.example", "macsec0")
mkad.start("./mkad.conf.example", ["macsec0", "macsec1"])
And stopped when desired (usually in test case teardown)
mkad.stop()
The MKAD will automatically negotiate MKA with the peer and establish the secure macsec channel to send the protected traffic.